Between August 2023 and April 2024, 2nd Brigade Combat Team, 10th Mountain Division was deployed across Iraq and Syria in support of Operation Inherent Resolve. During that time, state-sponsored militia groups launched over 170 attacks against a small network of coalition bases that 2/10 was responsible for defending. The brigade’s deployment represents the most recent and direct experience of any US Army unit defending against drone attacks and, consequently, an important set of lessons on countering and defending against rockets, missiles, and drones of all sizes.
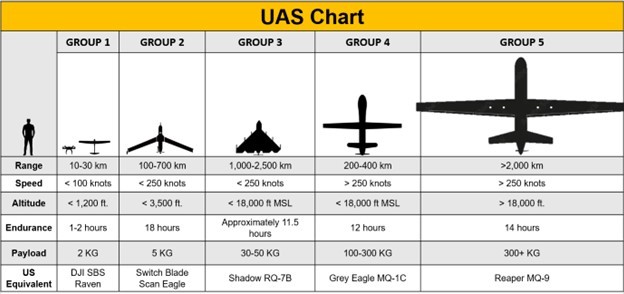
The soldiers of 2/10 experienced a wide range of enemy attacks against conventional munitions, from rockets and mortars to cluster munitions and short-range ballistic missiles. But the enemy’s weapon of choice was the one-way attack unmanned aircraft system (OWAUAS). These drones were mostly little, propeller-driven, fixed-wing craft made of carbon fiber, metal, and plastic. They flew low, sometimes less than a hundred feet off the ground, and depending on the type, their wingspan was a few feet to a few meters. Their US military equivalents are between a Scan Eagle and a Shadow. These systems have no landing gear because they’re designed to land on their noses with a bang.
The low-flying, low-cost, highly accurate, and prolific drones are irresistibly effective. Despite their small size, one-way attack drones on the battlefield today have tremendous range. Small to mid-sized one-way attack OWAUAS can travel as far as 2,500 kilometers, distances more akin to land attack cruise missiles and ballistic missiles than any tube-based artillery. Their versatility, reach, cost, and precision will increasingly make them appealing options for any modern combatant, no matter its global stature or military size.
Drawing out the Lessons for Large-Scale Combat Operations
In one sense, 2/10 experienced an unprecedented number of air attacks. In a few short months, 2/10 accumulated more combat experience in defending against OWAUAS than any unit in the Army. Yet this experience may soon seem miniscule compared to future conflicts. The number of attacks 2/10 handled over four months could conceivably occur in just a few days—or less. In Ukraine, for example, Russia has launched dozens of drones in single strikes. The US Army should prepare to encounter this frequency and scope of attacks in a future large-scale combat operations (LSCO) fight.
Context matters. The soldiers of 2/10 were employed in a very distinct role, defending from established fixed sites with reliable connectivity, hardened bunkers, and air mobility that was limited by electromagnetic interference, adversary surface-to-air weapons, and political constraints but still only partially contested. Most importantly, 2/10’s fight was a purely defensive one. Even when some of the counter–unmanned aircraft systems (C-UAS) capabilities were designed to be mobile, they were employed as part of a static defense. The base defense operations centers were well established and operated in controlled environments.
The attacks were continual but measured, nothing like the artillery barrages that Russia employs in Ukraine or what we know is possible for drone swarms from a well-supplied enemy. The OWAUAS salvos against 2/10 came mostly in singles and doubles. Rockets and missiles came in sporadic batches, sometimes a little over a dozen at a time. The consistent but low volume attacks were by the enemy’s design under the unique circumstances of the conflict. Thomas Friedman described the conflict as a “shadow war” and “the most dangerous game of chicken going on anywhere on the planet today” after visiting several CJTF-OIR (Combined Joint Task Force–Operation Inherent Resolve) outstations with the commander of US Central Command in February 2024. Escalation was carefully managed on all sides to apply pressure as part of a campaign of coercion. The types of attacks that 2/10 experienced were distinct to this particular conflict, which itself does not represent what the US Army will face during LSCO.
Still, we must pull lessons where we can, not least because artillery and aerial attacks will dominate in the next fight. Sifting through the unique characteristics of the C-UAS fight that 2/10 experienced in OIR reveals fundamental characteristics about C-UAS operations that need to be captured and applied to US Army operations.
The Three Types of Defenses: Kinetic, Nonkinetic, and Shelter
At the end of the day, there are three ways to defend against one-way attack drones: you can shoot them down, you can hit them with electronic interference, or you can seek shelter and absorb the hits.
Shooting a drone down using kinetic defeat comes in the form of missiles, guns, and directed energy lasers. Nonkinetic electronic defeat options vary depending on how the drone is controlled. The effects vary as well. If the drone is actively piloted, you can target the link between the ground control station and the aircraft. If the drone is GPS-guided, you can target the link between the GPS and the satellite. The enemy is constantly adapting technology and probing vulnerabilities in sensors and radar coverage. In just nine months, 2/10 saw advances in attack vector choice, GPS hardening, and other adaptations.
Seeking shelter varies by type of operation. In a deliberate defense, it means going to reinforced bunkers. On the offense or a hasty defense, shelter might vary from a rapidly dug foxhole to occupying a hard clad building or commandeering a basement or cellar.
All of these methods of defense rely first and foremost on detection. Bunkers only work if you’re inside one. You can only alert personnel to occupy a bunker if your sensors detect the threat with ample time and your alerts systems are working properly. The earlier you detect a threat (drone, rocket, missile, or artillery), the sooner you can alert the force to seek shelter while the air defense operators work to employ their systems to defeat the threat.
Overall, like any other battle plan, C-UAS operations are a multilayered multifaceted defense in depth. The best way to protect the force is through a combination of both active and passive defensive measures. Below are some observations on these different measures for leaders to consider.
Kinetic Defeat Considerations
Each kinetic option has limitations and constraints, just like any other weapon system. Missiles are most effective at range and provide standoff distance, but different systems have different time requirements to engage a threat. Patriot batteries have the best range and altitude but are designed for ballistic missiles and defense against high-performance aircraft (jets and Group 4–5 drones).
There are smaller missiles designed specifically for low- to mid-altitude drones (Group 1–3) and low-performance, principally propeller-driven aircraft. These drone interceptors range beyond ten kilometers with the right terrain and radar coverage. Initial missile variants took an uncomfortable amount of time to spin up before being ready to launch. But when these missiles do find their targets, they produce impressive displays of aerial acrobatics and precision.
These short-range air defense missiles were lifesavers for 2/10’s C-UAS fight, but they have important limitations in a LSCO context. Producing these missiles is a sophisticated and labor-intensive effort. Current missile variants can cost upwards of $100,000 each, about ten times the cost of each drone they defeat. Manufacturing outputs are sufficient for the consumption rates in OIR, but a future conflict could see an exponential demand for such systems on a global scale.
Guns, like the C-RAM (Counter Rocket, Artillery, Mortar), are more responsive and cost efficient than missiles, but their range is uncomfortably close. The Land Phalanx Weapon System (LPWS) fires 20-millimeter self-detonating rounds from a six-barrel Gatling gun. The LPWS is a variant of the Navy’s Phalanx Close-In Weapon System originally designed in the 1970s. As the name implies, it is only capable of defending against immediate threats (roughly within one kilometer). The LPWS operates on a trailer, with a limited mobile application, and is best used to defend key nodes rather than mobile troop formations at the edge of battle.
Directed-energy weapons are steadily emerging on the battlefield to complement traditional kinetic defeat options. During its deployment, 2/10 tested and employed several early variants of these short-range, directed-energy systems as both fixed-site and mobile platforms. They are futuristic and impressive in concept but work more as a slow burn than a Star Wars weapon. A laser might knock a drone out of the sky or deflect it enough to miss the intended target, but it might also just singe the paint off the drone before it dives into its destination. The drone’s distance, speed, and construction material, combined with the laser’s power output, time of acquisition, and target-lock capability, will determine effectiveness.
The US Army will face constraints with the employment of lasers in a LSCO environment. The amount of available power is important, so austere sites and mobile systems for land applications will require more technological advancements. Moreover, directed-energy weapons are hard to ruggedize and rely on sensitive components to concentrate the energy for effects.
Therefore, lasers have a promising future in the Army’s C-UAS arsenal, but they are still in the early stages of development and fielding. Their dispersion across the battlefield will depend on advancements in mobile power generation and whether the systems can be built to withstand the rough-and-tumble nature of combined arms maneuver.
Nonkinetic Defeat Considerations
There are several benefits to nonkinetic electronic warfare (EW) systems in the C-UAS fight, but these also have several important limitations and nuances. Electronic defeat equipment works by disrupting the link between the drone and the control station or by interfering with the drone’s navigation. Operationally, 2/10 found these systems most effective against smaller drones, especially commercially developed quadcopters and reconnaissance drones controlled by a ground station. When OWAUAS are guided by preprogrammed waypoints, some electronic countermeasures might still work, but kinetic defeat options are currently more effective.
A key consideration that 2/10 faced when employing various forms of EW was the secondary effect some electronic weapons can have on friendly communication systems. Some EW platforms use radar detections to target specific drones or interrupt select frequencies to redirect or disable drones outright. If these precision options are not available or not effective, other EW countermeasures include broad electromagnetic interference capabilities. Like any other electronic countermeasure system—for example, Duke systems designed to defend against improvised explosive devices—C-UAS EW platforms require regular updates and new fills to stay up with the regional threats.
Note that while more powerful EW measures can achieve the desired results, the effects sometimes come at a cost. Emitting a powerful electromagnetic interference (EMI) burst can be like chemotherapy for the radio waves. Some systems can zap everything in range and may just as readily interfere with friendly electronic and communication devices as with enemy signals. If the base or site’s sense-and-warn systems rely on wireless signal traffic, an electromagnetic interference burst may sever the signal to alert friendly forces of the incoming threat.
As these electronic countermeasures continue to transform, their effectiveness will ebb and flow, and opponents will evolve their shielding against electromagnetic interference. The frequencies and terminal guidance methods will change. It will be no different than the twenty years of improvised explosive device adaptations that the US Army defended against in Iraq and Afghanistan. It will be the same game, but with the threat now coming from the sky, not the ground.
Seeking Shelter: A Matter of Bunkers and Warnings
Despite all the expensive technology involved in defeating drone threats, some of the simplest and cheapest options—like sandbags and concrete—are still among the best protection measures. Bunkers remain an essential component to static defenses. The men and women of 2/10 can attest that as crude as they are, they work—as long as people were inside them.
The members of OIR spent considerable time in bunkers during 2/10’s deployment—sometimes multiple times a day or for hours at a time, depending on the threat. Seeking shelter became instinctive when the initial static was heard from base speakers. Soldiers and civilians came to accept the process, because these bunkers were 100 percent effective at saving lives, including instances where bunkers took direct hits from OWAUASs.
The combination of bunkers and radars were sometimes as important as concrete T-walls to 2/10 in the C-UAS fight. T-walls contain an unexpected blast from spreading and interfere with flight paths but offer no overhead coverage. Overhead protection, including reinforced bunkers and pre-detonation roofing on select buildings, were extremely important as attacks became more precise and targeted toward high-occupancy areas and key command nodes.
Bunkers came in various styles and designs, but most were concrete “C-channels” averaging six feet high and eight inches thick.
On their own, these three-sided structures are insufficient against most OWAUAS warheads and 107-millimeter rockets. Sandbag parties became the norm to reinforce C-channel bunkers with layers of sandbags or HESCO barriers. When available, the end caps were protected with welded steel doors or surrounded by mid-height concrete barriers. If you can see out of the bunker, the shrapnel can find its way in.
A good radar network tied to an effective sense-and-warn system provides advanced warning of a threat for personnel to seek shelter. On fixed sites, sense-and-warn systems can include speaker towers and indoor speaker boxes; audible coverage should be sufficient to alert someone in the shower or wake up sleeping personnel in all occupied zones of the base. In an offensive maneuver scenario, radio calls and mobile speaker boxes may need to suffice, but the expectation for rapid notification across the formation must remain the same.
Notification times will vary based on the threat. Some of the larger, fixed-wing drones were detected several minutes out, allowing sufficient time to seek shelter. Some threats get masked by terrain or hidden within a congested air picture (especially by airfields). In such instances, incoming drones were detected just seconds away from the base, providing time only to brace for immediate impact. Quadcopters and other small drones may be launched near a base to close in on a target in seconds. It may seem minor but the specific terms used by the system to communicate the threat are important and must clearly and immediately indicate what action personnel must take—whether to brace for immediate impact or seek shelter, for instance.
Notification systems provide other uses. “Big voice” systems help transmit guidance to sheltered personnel who lack any other means of communication. Announcements can instruct personnel to remain in bunkers, prepare to defend against a ground attack, deploy select response personnel, or begin unit accountability protocols. Like a fire drill in school, people go to shelter as they are, at whatever moment the alert is triggered. They might not have communication devices. They might not have pants. So sense-and-warn systems become an essential command-and-control feature in C-UAS fights.
The Limitations of Dismounted Systems
There are several dismounted systems available for both kinetic and nonkinetic defeat. These can fill critical gaps for the close-combat force but there are some important limitations to recognize about deploying these systems to defeat UAS threats.
Dismounted kinetic options include man-portable air defense systems (MANPADS) such as shoulder-fired Stinger missiles. It is important to weigh whether a dismounted Stinger team has the right training, equipment, and situational awareness to be effective against a drone attack. For example, does the MANPAD includes a day and a night sight? Soldiers may improvise by zip-tying a thermal optic to the Stinger, but that is a hasty measure at best. It is also important to understand how portable missile systems acquire and lock onto targets. Stingers are heat-seeking missiles designed to destroy helicopters and airplanes. Smaller drones may not produce the requisite heat signature to acquire “tone” with a Stinger. Also, it is important to appreciate the different variants of surface-to-air missiles. Common Stinger variants are point-detonation weapons while others are air-burst munitions. It is less likely that a point-detonated Stinger will intercept a small, low-heat-producing drone.
Nonkinetic choices available today produce directed electronic interference and defeat options with portable devices that often give off strong Starship Trooper vibes. Current “shoulder-fired” systems are useful for intercepting small quadcopters loitering overhead and conducting observation but dismounted nonkinetic C-UAS systems have limited effectiveness in defeating fast-approaching attack drones.
There are several risks to deploying dismounted teams to defeat drones. If these soldiers are not integrated with a radar network and are reliant on visual target acquisition, the risk of hitting a friendly aircraft by mistake increases. This is especially high when operating near airfields or friendly air corridors. Ideally, C-UAS systems will advance to the point where dismounted troops at the front edge of battle can employ MANPADS as part of an integrated radar network that covers the friendly force. Until then, leaders should be clear-eyed about what they may achieve (or risk) by deploying Stinger teams against OWAUAS threats. Having dismounted teams on the berm, rather than in bunkers, may feel prudent without actually being effective. Commanders must carefully consider the characteristics of the handheld equipment available to ensure it matches the anticipated drone threats.
The Engagement Process
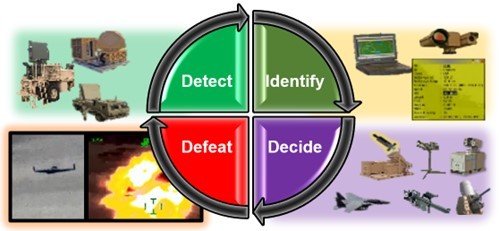
Employing these air and missile defense systems follows all the same fundamentals of any traditional defense in depth, just with a few added variables. Success depends on a unit’s ability to find and characterize threats with sufficient time to employ a hodgepodge of layered defense systems. That activity is best understood through the C-UAS process of detect, identify, decide, and defeat.
Redundant and overlapping radar systems detect air tracks as far out as possible. Battle captains then establish positive identification (typically through digital means, as most tracks populate beyond the visual range) and decide on one or more kinetic or nonkinetic means of defeating the threat.
In the current base-centric OIR mission, this process is conducted solely by the base defense operations center (BDOC), defined in joint doctrine as “a [command-and-control] facility established by the base commander as the focal point for [force protection], security, and defense within the base boundary.” The BDOCs operated by 2/10 at multiple bases throughout Syria and Iraq proved the value of having established crews in hardened command posts with connectivity and access to multiple intelligence, surveillance, and reconnaissance platforms. The BDOC construct is effective at employing the C-UAS process; static and redundant radar systems enable early detection and positive identification of threats, rapid decision about engagement platform, and successful defeat by missile, LPWS, laser, or EW. In a LSCO fight, ground force commanders must maximize their ability to not only command and control their formations, but also execute this ever-changing air defense battle drill with varying systems.
The transitions from base commander to maneuver commander, from base boundary to area of operations, and from fixed-site command post to mobile command post are worth contemplating. The Army is fielding several movable radar and interceptor systems and actively developing new systems to be tested soon. Regardless of what equipment shows up on the hand receipt, we would be wise to understand, implement, and test to provide feedback and tailor the tools to our mission end states.
The personnel and equipment requirements for the C-UAS battle drill are in direct conflict with the understandable pressure on ground force commanders to reduce the size and electromagnetic signatures of their command posts. Even a reduced battalion or brigade command post typically encompasses multiple vehicles, generators, antennae, and tentage or shelters. At a minimum, the C-UAS fight means additional data entering the existing command post, and an added layer of decision requirements and stress.
Dispersion complicates the issue further; much of 2/10’s C-UAS success was a direct result of colocating a team of nine or more BDOC personnel to monitor multiple radar systems, clear air, communicate across a base (and report upward), and conduct emergency response. A unit in LSCO may not have the luxury of colocating such teams.
Observations from Transforming in Contact
Counter-UAS systems will continue to transform and adapt for years to come. The soldiers of 2/10 lived through the experience of transforming in contact and gained some important insights worth sharing. The vignettes below describe specific issues that may not be precisely replicated in future operational environments, but they are shared to highlight some of the subtle challenges that transforming in contact creates.
Testing New Equipment on the Real McCoy
Prototype equipment was regularly tested by 2/10 during the deployment, including directed-energy lasers and various C-UAS missile systems. Live-fire tests involved model Group 1–3 UAS test drones. The bodies of these drones were not made of the same materials as enemy drones. Live-fire experiments gave a false sense of confidence in the effectiveness of the prototype weapons because these friendly UAS were easier to shoot down than the enemy drones. It is important that validation test fires include replicas of enemy systems to ensure that the prototype equipment has the desired effects.
Bearing, Altitude, Range, and Speed
The contact report in a C-UAS fight is called “BARS”—referencing the bearing, altitude, range, and speed of a suspected track. Radar systems often provide this data well before a unit can gain visual identification with current camera systems. The combination of these four elements helps leaders and operators distinguish between birds, balloons, OWAUAS, and friendly aircraft. Sometimes the altitude is the critical factor (only certain airframes can fly at thirty thousand feet) or the speed is too slow to be a fixed-wing drone. Range helps leaders understand time available to react. BARS needs to become a familiar concept the same way SALT and SALUTE reports became common knowledge across the Army.
Fourteen Clicks
Early versions of the radar software included cumbersome interfaces. Radar operators found themselves needing to perform up to fourteen clicks of a mouse to interrogate suspected tracks and deploy countermeasures during an engagement sequence. Such a laborious interface would create a deadly flaw against a swarm scenario. As operators identify these sorts of inadvertent inefficiencies built into the software, development engineers need to be informed to quickly update programs.
Knowing the Default Settings on Systems
For several months, close engagements ended prematurely with missiles terminating before hitting targets because OWAUAS were getting too near to the base. C-UAS missiles were self-detonating or refusing to launch altogether based on default engagement settings programmed into the software. Such well-intended safety features created by software engineers were not well communicated to commanders in the early stages of the conflict because the issue had never arisen before. Once the settings were explained and understood, commanders were able to adjust them on a case-by-case basis based on the commander’s risk considerations. This greatly improved the kill ratio of the C-UAS engagements afterward. As new systems are fielded, programmers and operators need to know which software features are fixed and which are adjustable. Theater commanders should have the knowledge, authorities, and technicians available to adjust settings as needed. As enemy tactics and weapons evolve, commanders need expedited flexibility to make the risk-reward calculus for system modifications.
System Performance Analysis
Program engineers from the Joint Analysis Team in Huntsville, Alabama routinely provided critical after-action feedback on the performance of missiles and radars during operations. These engineers could determine the effectiveness of radar placements and diagnose issues when missiles failed to hit targets. Though the quality of their work was first class, they were far from the battlefield and access to their teams was at times delayed. The Army needs to ensure support teams are sufficiently staffed and accessible to meet the demands of battlefield commanders. If that means deploying engineers and software design teams forward, the Army should do so, especially for novel systems still undergoing field testing and evaluation. This is literal rocket science after all, and the fight evolves at combat speed. The whole team needs to be together to stay ahead of the enemy.
An Overreliance on Field Service Representatives
The other side to continually testing and evaluating systems is the over reliance on field service representatives (FSRs) for many of these new systems. Some FSRs are barely more knowledgeable than soldiers on the equipment, but contracts required FSRs to perform installation, maintenance, and reloading operations. Soldiers, not civilian contractors, should be installing, fixing, and reloading equipment in combat—especially in large-scale combat operations. Yet reducing FSR reliance is easier said than done. We have all felt the pain of training a soldier to understand a new Army system, only to lose the capability to another unit before knowledge proliferates. Civilian FSRs are sometimes more permanent than military personnel and can be better resourced and trained to maintain and improve complex systems. Technical equipment requires formal education and hours of hands-on learning in the field, something most units struggle to sustain. We owe units a sound plan for fielding and maintaining C-UAS systems, and acquiring the skill to employ them effectively before they end up permanently parked in the motor pool.
The recent combat experience gained in Iraq and Syria remains the most significant US C-UAS fight to date even, if it will one day seem miniscule compared the future LSCO fight. Therefore, like a preseason matchup, any good sports team would use the experience to prepare for the long season ahead. And because the attacks 2/10 faced came repeatedly over a four-month period, across a variety of locations, each with different characteristics, the value of the empirical and quantitative data collected by the brigade makes the experience truly valuable to share with the force across operational domains.
As a reminder, the experience of 2/10 was purely a defensive fight. The challenges of performing C-UAS in the offense for a mobile fight are amplified. The current arsenal of missile interceptors, radars, directed-energy lasers, and nonkinetic defeat systems were only tested in fixed-site settings. The notion of establishing a layered air defense against Group 2 and 3 OWAUAS for major attacks like a wet gap crossing would require significant adaptations to the methods developed by 2/10 in OIR.
Still, static defense against OWAUAS will also remain relevant in future conflicts. Key theater support nodes like airports and seaports of debarkation will always serve as high-payoff targets within range of drone attacks. The UAS variants intercepted by 2/10 were often launched hundreds of kilometers from their intended targets. Attack drone ranges and payloads will continue to increase over time, so no matter how mobile frontline troops are in a LSCO fight, rear areas will need robust C-UAS defenses as well.
The C-UAS fight in CJTF OIR was a true example of what the chief of staff of the Army describes as transforming in contact. Consistent evaluation and testing by leaders across the tactical level was critical. Junior leaders found creative ways to isolate variables and test them. They could not just trust that the “green” status on a dashboard was good enough. They had to anticipate the next threat, then start adjusting and understanding their equipment. When select outstations began discovering new solutions, the unit organized weekly review sessions over secure teleconference video calls to spread lessons across the formation. It became a race for information as the enemy continually adapted against our defensive measures in real time.
The defense by 2/10 against more than 170 attacks from state-sponsored militia groups can help orient leaders to the challenges that the US military will face in future conflicts. Combat will continue to evolve, but the principles and insights outlined above are meant to accelerate the learning curve and highlight concerns for maneuver formations as our enemies push us toward a multidimension fight.
Lieutenant Colonel D. Max Ferguson is a career infantry officer with six deployments to Iraq, Afghanistan, and West Africa with both conventional and special operations units. He earned a PhD in public policy from the University of Texas at Austin as a Goodpaster scholar with ASP3. He currently commands 2-14 IN, 2nd BCT, 10th Mountain Division and commanded FOB Union III in Baghdad, Iraq in support of CJTF-OIR from August 2023 to April 2024.
Lieutenant Colonel Russell Lemler is a career field artillery officer with experience in Afghanistan, Jordan, Iraq, Syria, and Gabon. He previously served in West Point’s Department of Behavioral Sciences and Leadership and holds a PhD in management from Columbia Business School. He commands 2-15 FA, 2nd BCT, 10th Mountain Division and commanded al-Asad Airbase, Iraq in support of CJTF-OIR from August 2023 to April 2024.
Authors’ note: Members of 2/10 have produced a volume of C-UAS lessons learned and technical details of the systems and tactics developed by the different outstations in OIR at the secret level of classification, including numerous C-UAS white papers and a forty-five-minute video focused on BDOC engagements. These products, along with the missile and radar data from all of the OWAUAS engagements, are now located on the Center for Amy Lessons Learned SIPR page. These products will be most valuable to units preparing to deploy now or in the years ahead, but like early smartphones and computers, the C-UAS systems tested and fielded in 2023 and 2024 will soon become obsolete and replaced by updated versions. Still, the archive of information, data, and insight to early combat applications of C-UAS will remain available for researchers, software engineers, and tactical leaders to analyze years from now. Leaders can find these documents on SIPR at https://dod365sec.spo.microsoft.scloud/teams/Army-TRADOC-CenterforArmyLessonsLearned.
The views expressed are those of the authors and do not reflect the official position of the United States Military Academy, Department of the Army, or Department of Defense.
Image credit: Spc. Christopher Brecht, US Army