In 1863, a Confederate agent named Thomas Courtenay devised a new weapon designed to sabotage Union steamships. Covered in pitch and rolled in coal dust, the explosive device was designed to look like a piece of coal. Courtenay hoped that Union steamship crews would unwittingly toss the disguised explosive into a vessel’s furnace, damaging or destroying the ship. Despite the inventiveness of the so-called “coal torpedo,” however, its battlefield effectiveness during the Civil War remains inconclusive as Confederate records were deliberately destroyed at the end of the war.
Courtenay’s coal torpedo reflects the fact that state and nonstate actors alike have turned to sabotage operations throughout history with the aim of secretly disarming, obstructing, or destroying enemy war materiel or infrastructure. Often the forces conducting sabotage have been either intelligence organizations or what today we call special operations forces (SOF). During World War II, the US Office of Strategic Services (OSS) conducted myriad sabotage operations spanning multiple theaters and domains. The OSS Maritime Unit, in particular, pioneered many tactics and techniques that would later become integral to modern naval special warfare. But despite this robust history, over the past twenty years the SOF community has primarily focused on conducting counterterrorism and counterinsurgency operations on land.
Today, as the US military shifts priorities from counterterrorism to strategic competition, SOF have begun to rebalance to focus on both countering violent extremist organizations and competing with peer and near-peer actors. In light of SOF’s history with sabotage and recent renewed interest in the subject (strategic sabotage was listed as a priority research topic for the Joint Special Operations University in 2020, for example), the time is ripe for an analytical examination of the subject. Maritime sabotage operations in particular deserve further study given the growing importance of maritime regions from the Indo-Pacific to the Black Sea.
Trends in Maritime Sabotage
In a recent report, the Center for Naval Analyses examined past instances of maritime sabotage to help inform policymakers, practitioners, and researchers. My coauthors and I built a dataset of unclassified instances of maritime sabotage to facilitate our analysis, then coded each event according to a set of variables.
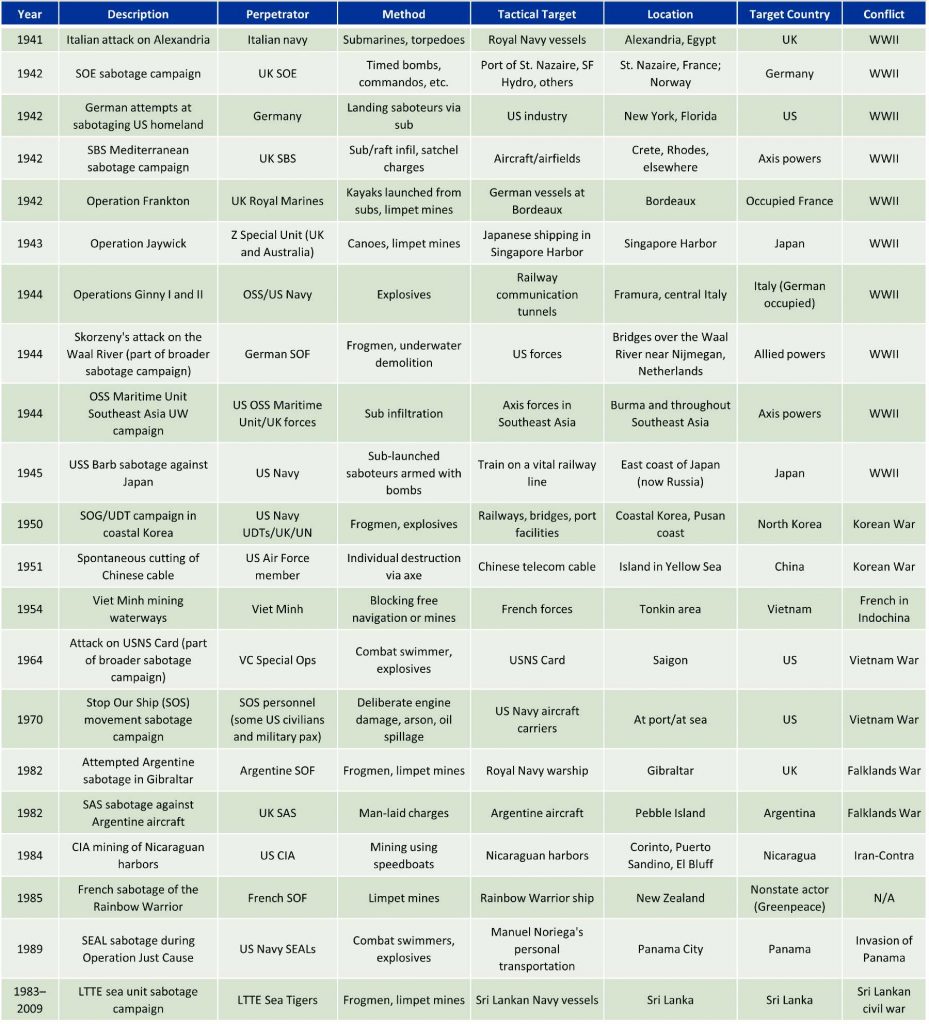
Overall, our study identified three main trends. First, maritime sabotage operations that incurred third-party collateral damage often led to significant negative political consequences for the perpetrators. In both the CIA’s mining campaign in Nicaragua in 1984, for example, and the French sabotage of Greenpeace vessel Rainbow Warrior the following year, the perpetrators faced withering political backlash. Incidentally, both of these sabotage operations occurred outside of large-scale combat operations, which may reflect the political danger associated with conducting sabotage operations outside of declared hostilities.
Second, and perhaps counterintuitively, losing the element of surprise did not seem to make a sabotage operation more likely to fail. Of the individual sabotage operations we examined in which the element of surprise was lost, approximately half still succeeded in achieving their desired tactical objectives. More broadly, our research suggests that maritime sabotage operations may be difficult to conceal, as exemplified by the high rate of force exposure. If true, this dynamic may give pause to policymakers wishing to employ maritime sabotage operations in sensitive environments.
Third, the more complex the maritime sabotage operation, the more likely it was to fail. We determined complexity by assessing the sabotage force (whether the operation was joint or combined), the equipment employed, and the relative ease or difficulty of the mission itself. The most complex sabotage operations tended to be associated with a greater rate of failure or led to significant unintended negative consequences (such as friendly casualties). For example, the attempted German sabotage campaign against the United States during World War II was extremely complicated, involving landing multiple teams of saboteurs by submarine at various points along the east coast. That operation failed when several of the saboteurs turned themselves in to American authorities and revealed the details of the plot in an attempt to avoid punishment after being compromised during the initial landing.
In addition to these three trends, our analysis enabled us to make several observations regarding the historical employment of maritime sabotage. World War II represents a high-water mark for maritime sabotage, with almost half of the identified instances in our dataset occurring during that conflict. Relatedly, most instances of maritime sabotage occurred during periods of large-scale combat operations. While this may be partly a function of our reliance on open-source information, it suggests that outside of declared hostilities, acts of maritime sabotage may be considered overly provocative.
Finally, in most maritime sabotage instances, the force employed was composed of SOF or similar personnel. The maritime sabotage operations we examined often involved the use of combat divers to emplace explosives. During the failed Operation Algeciras in 1982, for example, rogue Argentine paramilitary divers sought to attach mines to a British warship in port at Gibraltar under the cover of darkness. Although foiled by local police and British intelligence (and perhaps an observant rental car proprietor who picked up on some sloppy tradecraft), the aim was an attack that would divert British naval resources from the Falklands. While the operation was unsuccessful, it underscores that sabotage operations typically require skill sets and capabilities that are most commonly found among SOF and SOF-like entities.
Implications
As the joint force explores new approaches for countering adversaries across the competition continuum, researchers and practitioners should not neglect the role of maritime sabotage. Three questions in particular should be a priority for further analysis moving forward.
First, there is no current official US Department of Defense definition for sabotage, even as sabotage has become an area of renewed interest for the military. This lack of a definition may serve as a limiting factor to creatively developing and employing sabotage operations in the future. As the DoD Dictionary of Military and Associated Terms notes, common terminology “enables the joint force to organize, plan, train, and execute operations with a common language that is clearly articulated and universally understood.” For our analysis, we defined sabotage as a mission (conducted via an individual act or as part of a campaign) to secretly disarm, obstruct, or destroy enemy war materiel or infrastructure for military advantage. DoD should consider whether this definition is appropriate for wider adoption. Grappling with these definitional questions will help policymakers better understand how sabotage operations might be employed in rapidly evolving security environments.
Second, the majority of maritime sabotage operations occurred during declared hostilities. Yet the United States is not currently in a state of large-scale combat operations, but rather an environment of day-to-day competition. DoD should therefore consider what role sabotage may play both in today’s environment, characterized by competition below armed conflict, and during periods of outright hostilities. Specifically, outside of large-scale combat operations, what additional military or political benefits and risks might sabotage operations entail? What authorities does DoD have to conduct such operations? And what potential escalatory effects might they have? Answering these questions will better prepare policymakers for the possibility of conducting sabotage operations in new and evolving strategic environments.
Third, the past two decades have witnessed the introduction of two new domains—space and cyberspace—into the DoD lexicon and command structure. Our dataset, being historical in nature, did not identify or examine any instances of cross-domain sabotage involving these new domains. In the future, however, cross-domain activities like those at the nexus of maritime and cyberspace will present great challenges and opportunities for the joint force. US policymakers should consider how to leverage maritime assets in support of sabotage across domains.
Sabotage is not a new concept. From Courtenay’s coal torpedo to Lawrence of Arabia and his indigenous partners’ sabotage of the Hejaz railway, sabotage has been consistently employed throughout history, with varying degrees of success. Today, if conducted successfully, maritime sabotage may be a way the joint force can challenge adversaries in both day-to-day competition and in large-scale combat operations. Yet sabotage also entails additional risks. Practitioners, policymakers, and researchers must think through the conceptual and practical challenges surrounding how sabotage operations could be employed before such operations become necessary.
Alexander Powell is an expert on SOF, terrorist group tactics, and counterterrorism. He has worked extensively on security issues in Afghanistan and has deployed there numerous times to conduct assessments of the Afghan National Defense and Security Forces. In 2017 Mr. Powell deployed with the Special Operations Joint Task Force–Afghanistan to help stand up the command assessment cell. His research on SOF has encompassed issues ranging from the strategic down to the tactical levels. This piece draws on an October 2021 Center for Naval Analyses report entitled “Maritime Sabotage: Lessons Learned and Implications for Strategic Competition” by Alexander Powell, Elizabeth Yang, Annaleah Westerhaug, and Kaia Haney.
The views expressed are those of the author and do not reflect the official position of the United States Military Academy, Department of the Army, or Department of Defense.
Image credit: Mass Communication Specialist 2nd Class Russell Rhodes Jr., US Navy



Mr. Powell,
I would suggest you add another area of focus to the above summary, and that is sabotage of subsea cables. These assets are critical to all aspects of commercial and national security operations, as noted specifically by the DHS and other Agencies..
This threat is real and current, and the Russians are particularly capable in this area.
If you would like to discuss this subject further, please feel free to contact me.
Steve Rosa
"A full moon and overcast skies were present the night before the start of the (Easter) offensive (March 31, 1972). Troop movement began with the 308th NVA Infantry Division and the attached 202nd Armored Regiment springing from the central DMZ towards Dong Ha and then continuing towards Quang Tri. Simultaneously, the 27th Independent Infantry Regiments and the 126th Naval Water Sapper Regiment jumped off from the eastern DMZ, attacking southwards between the area east of QL-1 and the South China Sea. This was not the first time that this unit conducted operations in northern I Corps. On January 2, 1971, Quang Tri Popular Forces captured at least 16 126th Water Sappers who were moving a 2,000lb Soviet mine southward from a position north of the DMZ." A member of the 126th was later captured in Hue during the Easter Offensive.
Break in the Chain Intelligence Ignored, page 61.
You might look into political and legal limitations on victim-operated mines to better flush out your article.
Much has changed since the days of the coal torpedo. In the explosives world, very little for the better.
Maritime sabotage does have its uses in wartime, or to prevent situations from escalating further in peacetime, but is maritime sabotage considered "a safe method" these days? Bear in mind, maritime sabotage is only effective if the perpetrator GETS AWAY WITH IT without an enemy response.
If the nation that conducted the sabotage is discovered, the ramifications can be immense, ranging from retaliation with hypersonics, cruise missiles, supersonic missiles, cyber attacks, tactical ballistic missiles, and other means of force. To employ stealth sabotage force means that the conducting nation must be prepared to employ more means of force if discovered and the offending nation should be aware that tensions and the situation can escalate. The saboteur cannot let the guard down if the targeted nation seeks revenge.
Would the slow, sneaky, stealthy way of SOF maritime sabotage be worth it if the enemy nation can fire hypersonic missiles that are blisteringly fast, showy, easy to detect, and will make the news as retaliation? This is not to say SOF maritime sabotage doesn't have a place in combat because it does, but the value of the target has to be weighed on what response the targeted nation might do if such an asset is lost. In 2022, there is no shortage of other weapons to seek retribution for the loss of an asset to sabotage and the offensive nation is discovered. Acts of war are just that and nations must be prepared for conflict if maritime sabotage were to occur without hostilities being declared.
A surgical strike with sabotage can do wonders to change the calculus of the scene…and yet some mass fire of missiles in retaliation can also achieve the same or a greater effect also in secret vs. conventional use of force.
Perhaps also consider the ease with which anyone could shut down a port: disable gantry cranes; introduce viruses and worms into port cargo management and ship systems; jam VHF channels used for navigation safety; obstruct or damage navigational aids; spoof LRIT and AIS; 'swarm' civilian craft into disputed, restricted, or sensitive area.
Any of these could rapidly bring a country's supply chain to a crashing halt, without one shot being fired, one person being hurt, or one ship being damaged. The ultimate 'grey zone' operational suite.